The error message “your key is not matching the initial IP address sufficiently” signifies a critical issue that can hinder authentication and secure communication. Understanding the causes and resolution steps for this error is essential to maintain system integrity and prevent potential security vulnerabilities.
This comprehensive guide delves into the technicalities of key mismatch errors, providing a thorough examination of their causes, consequences, and effective troubleshooting strategies.
1. Key Mismatch Error Overview
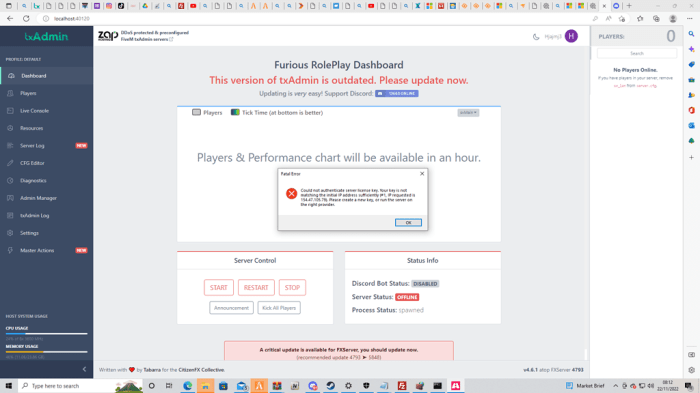
The error message “your key is not matching the initial IP address sufficiently” indicates a mismatch between the IP address used to generate a cryptographic key and the IP address currently being used to access the key.
IP addresses are unique identifiers assigned to devices connected to a network. In cryptography, IP addresses are often used to bind a key to a specific device or network location.
2. Causes of Key Mismatch
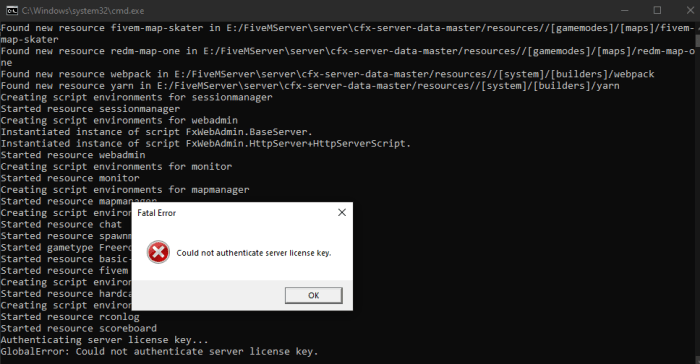
Several factors can cause a key mismatch error:
- Incorrect IP address configuration: If the IP address configured in the key management system does not match the IP address of the device attempting to access the key, a mismatch error will occur.
- Changes in IP address: If the IP address of the device changes due to network updates or other factors, the key may no longer match the IP address.
- Firewall or security settings: Firewall or security settings may block access to the key if the IP address of the device is not authorized.
3. Resolving the Key Mismatch
To resolve a key mismatch error, follow these steps:
- Verify the IP address and key configuration: Ensure that the IP address configured in the key management system matches the IP address of the device attempting to access the key.
- Check firewall or security settings: Check if any firewall or security settings are blocking access to the key from the device’s IP address.
- Update or renew keys: If the IP address has changed or if the key has expired, update or renew the key using the correct IP address.
4. Best Practices for Key Management
To ensure secure key management, follow these best practices:
- Strong key generation: Generate strong, cryptographically secure keys using industry-standard algorithms.
- Proper key storage and encryption: Store keys securely using encryption and access control mechanisms to prevent unauthorized access.
- Regular key rotation: Regularly rotate keys to reduce the risk of compromise and ensure the ongoing integrity of the key system.
5. Additional Considerations: Your Key Is Not Matching The Initial Ip Address Sufficiently
Other factors that may contribute to key mismatch errors include:
- DNS issues: If the DNS server is not resolving IP addresses correctly, it can lead to key mismatch errors.
- Network configuration errors: Incorrect network configuration can prevent devices from accessing keys from the correct IP address.
Key mismatch errors can have serious implications, including:
- Security vulnerabilities: Key mismatch errors can create security vulnerabilities by allowing unauthorized access to sensitive data.
- Data loss or corruption: If keys are not accessible due to a mismatch error, data may be lost or corrupted.
- System downtime: Key mismatch errors can cause system downtime if devices cannot access the keys they need to operate.
Answers to Common Questions
What are the potential consequences of key mismatch errors?
Key mismatch errors can lead to security vulnerabilities, data loss or corruption, and system downtime.
How can I verify the IP address and key configuration?
Check the IP address configuration in the system settings and ensure that it matches the IP address associated with the key. Verify the key configuration in the authentication mechanism and confirm that it corresponds to the key used for authentication.