
All Modern Programming Languages Contain Many Methods That Are Predefined
All modern programming languages contain many methods that are predefined, providing a rich and powerful toolkit for developers. These methods offer a wide range of functionalities, from input/output operations to…
Read more »
In Multi Channel Funnel Reports How Are Default Conversions Credited
In multi channel funnel reports how are default conversions credited – In the realm of digital marketing, understanding how default conversions are credited in multi-channel funnel reports is paramount. This…
Read more »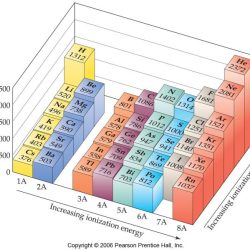
Arrange The Elements In Decreasing Order Of First Ionization Energy
Arrange the elements in decreasing order of first ionization energy. This topic delves into the fascinating world of ionization energy, a fundamental concept in chemistry that governs the behavior of…
Read more »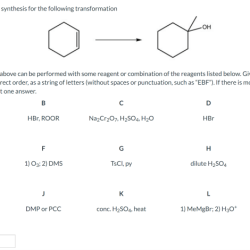
Propose An Efficient Synthesis For The Following Transformations
Propose an efficient synthesis for the following transformations – Proposing an efficient synthesis for the following transformations sets the stage for this enthralling narrative, offering readers a glimpse into a…
Read more »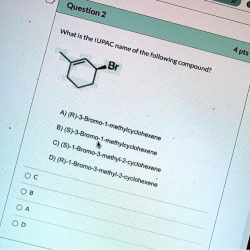
Rank The Following Compounds In Order Of Increasing Stability.
Rank the following compounds in order of increasing stability. Chemical stability is a crucial concept in chemistry, determining the behavior and applications of compounds. Various factors influence stability, including molecular…
Read more »
Your Key Is Not Matching The Initial Ip Address Sufficiently
The error message “your key is not matching the initial IP address sufficiently” signifies a critical issue that can hinder authentication and secure communication. Understanding the causes and resolution steps…
Read more »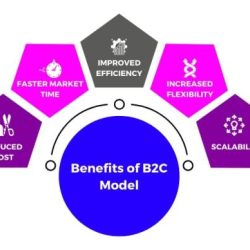
Online Firms Like Amazon.Com That Take A B2c Model Approach
Online firms like Amazon.com that take a B2C model approach set the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and…
Read more »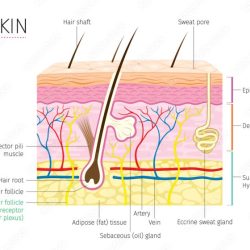
Table 6.1 Model Inventory For The Integumentary System
Table 6.1 Model Inventory for the Integumentary System stands as an indispensable resource, providing a comprehensive overview of the integumentary system’s structure, function, and clinical significance. This meticulously crafted table…
Read more »
The Company’S Shipments Of Newly Produced Branded
The company’s shipments of newly produced branded products offer a window into the company’s performance, market position, and growth prospects. This comprehensive analysis examines the data, trends, and factors that…
Read more »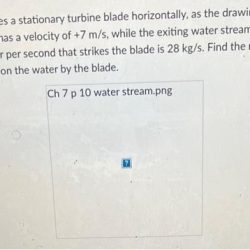
A Stream Of Water Strikes A Stationary Turbine
A stream of water strikes a stationary turbine, setting in motion a captivating journey into the realm of hydroelectric power generation. This enthralling narrative delves into the intricate workings of…
Read more »